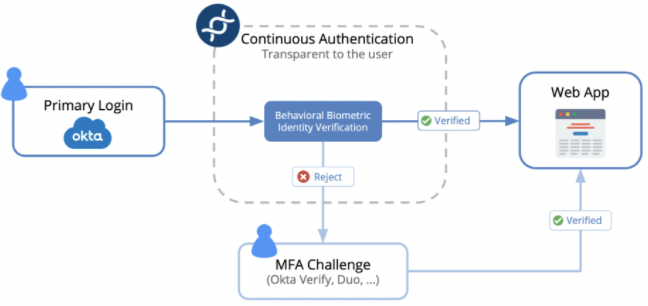
Integrate Twosense with your Existing MFA Solution

The First Line of Defense
When Twosense can confirm a user's identity with behavioral biometric MFA, no further multifactor challenge is needed. Most multifactor solutions are supported as a second factor.

"MFA is something everyone loves to hate, but it’s necessary and people get it,” he said. “With Twosense we are able to make that necessary evil a little less evil.”
- Taylor Higley, Director of Information Services, American Federation of Government Employees

MFA Interruptions by the Numbers
On average, employees lose 18.96 hours per year to IT security procedures, and that does not take into consideration the roughly 15 seconds per MFA check completed successfully. Twosense automates the challenge-response of multi-factor authentication on behalf of its users by using machine learning to drive passive biometrics that can guarantee a user's identity.
Increased Interruptions Mean Decreased Productivity
Flow state has been shown to increase productivity by an astonishing 500 %, but it is as fragile as it is powerful. Studies indicate that it can take roughly 30 minutes of uninterrupted focus on a task in order to achieve a state of flow, and when interrupted can take on average 25 minutes to get back into the original task, plus up to an additional 30 minutes to regain the flow state so they can be fully productive again.

Organizations with engaged employees experience a variety of benefits
With security controls being reported as one of the biggest contributors to job satisfaction and with employee turnover at an all-time high in 2021, organizations simply cannot afford to interrupt their employees throughout the day.
Up to 43% less turnover
10% higher customer loyalty
23% higher profitability
18% higher productivity

Choose both maximum security and minimal user friction.
CISOs have long been faced with a dilemma - security, or convenience? Aggressive MFA policies cause user complaints or incentivize employees to bypass security policies. With user interruptions no longer a factor in security decisions, a user’s identity can be confirmed repeatedly and constantly throughout the day.