Introduction
In a recent security horror story, KnowBe4, a renowned security awareness training company, hired a seemingly qualified senior software engineer. However, this new hire was an AI deepfake, a North Korean agent. Fortunately, within the first 45 minutes of their “work,” the KnowBe4 team detected a surge of malware on the engineer’s company-issued laptop, allowing them to swiftly neutralize the threat.
This incident underscores a terrifying reality—no organization is immune to such risks. What happened to KnowBe4 could easily happen to a Business Process Outsourcing (BPO) company, where the consequences might be even more catastrophic.
This blog will explore how a similar scenario could unfold within the BPO industry, the inherent vulnerabilities in human-centric security protocols, and why traditional biometric solutions may not be sufficient. We’ll also discuss how behavioral biometrics, provided by solutions like Twosense, could prevent such internal and external security breaches.
The BPO Dilemma: Outsourcing Security Risks
The KnowBe4 incident illuminates a broader issue—how easily a threat actor can infiltrate an organization, even one with robust security measures. BPOs, by their nature, are particularly vulnerable. These organizations outsource tasks and hire employees often remotely, and in an industry where turnover is a persistent challenge. This setup can lead to a myriad of problems, not least of which is the risk of agents outsourcing their work to others.
This problem has escalated in the post-pandemic world, where remote work has become the norm. Without the physical presence of employees in a centralized location, BPOs struggle to ensure that the person they trained is the same person handling calls once training is complete. Many have tried to counter this issue by leveraging cameras to verify agent identity. However, this quickly became a privacy issue and has since been deemed illegal in some regions, such as Colombia. The rise of “shadow BPOs”—unauthorized mini-call centers operated by individuals hired by the BPO—has become a significant threat. Employees may hire others, often unqualified, to perform their work, compromising the quality and security of the service provided.
The Waterfall of Malicious Intent
At its least malicious, an employee might let a friend or family member clock in for them to meet attendance requirements. But this can quickly escalate. In some cases, employees may outsource their entire job, pocketing a portion of the salary while someone else does the work. The most dangerous scenario is when an insider colludes with an outsider—a hacker or a state-sponsored actor—granting them access to the BPO’s client's systems. This puts the BPO at risk and endangers their clients, who trust the BPO with their sensitive data.
These insider threats, whether motivated by laziness, greed, or malice, are an existential problem for BPOs. The trust between a BPO and its clients is the foundation of the industry. If that trust is broken, the entire business model is at risk.
Biometrics: A Double-Edged Sword
To combat these risks, many organizations turn to biometric authentication—fingerprints, facial recognition, and other forms of identity verification. On the surface, this seems like an effective solution. After all, biometric data is unique to the individual, making it harder for unauthorized users to gain access. However, the reality is more complex.
Most biometric systems rely on technology owned by third parties, like Apple’s Face ID or Google’s fingerprint recognition. While these systems are secure, they are tied to the user’s device and account with the technology provider, not the employer’s identity system. A determined and complicit user could enroll another person’s biometric data—such as a family member’s face or fingerprint—to bypass the intended security measures entirely.
Moreover, the cost of implementing robust biometric systems is often prohibitive. It requires specialized hardware and software, which can be expensive and challenging to manage at scale. Even with these systems in place, they only verify the user at the start of a session, leaving long gaps where unauthorized access could still occur.
Behavioral Biometrics: A Subtle Yet Powerful Solution
Given traditional biometrics' limitations, a more nuanced approach is needed—one that can continuously verify the user’s identity throughout their session. This is where behavioral biometrics comes into play. Unlike traditional biometrics, which rely on physical traits, behavioral biometrics analyze patterns in how an individual interacts with their device—such as typing speed and mouse movements.
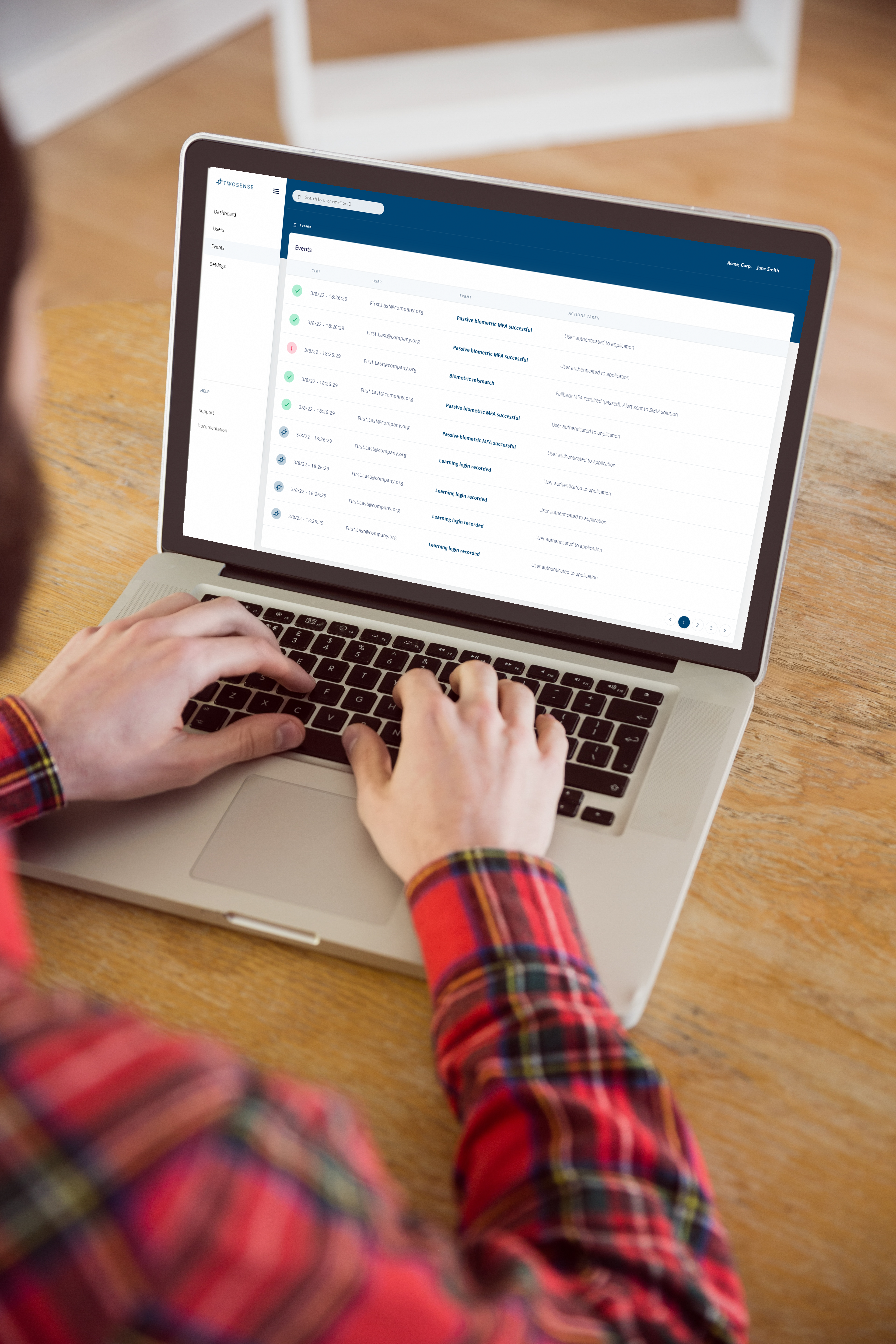
Twosense, a leader in this field, offers a solution that integrates seamlessly into BPOs' existing workflows. Twosense can detect unauthorized users in real time by continuously monitoring behavioral patterns and flagging when their behavior deviates from their behavioral model's norm. This makes it much harder for an unauthorized user to take over someone else’s work without being detected.
The real power of behavioral biometrics lies in its subtlety and continuous nature. Unlike traditional biometrics, which can be gamed or bypassed, behavioral biometrics are a constant safeguard, invisibly monitoring in real time without disrupting workflows. There is no need for extra hardware or intrusive surveillance—just a lightweight software layer that ensures the right person is at the keyboard every second of their shift. This proactive, always-on verification directly addresses the risks posed by insider threats, shadow BPOs, and collusion with external actors. It's not just about improving security; it's about transforming it—turning every interaction into an opportunity to prevent fraud, protect client data, and preserve trust.
Conclusion: Mitigating the Invisible Threat
The KnowBe4 incident is a chilling reminder of the vulnerabilities that exist even in well-secured environments. For BPOs, the risks are magnified by the very nature of their business. Outsourcing is their strength and their Achilles’ heel, creating opportunities for internal fraud and external threats.
Traditional security measures, including biometrics, offer some protection but are ultimately limited by reliance on physical traits and single-point-in-time verification. Behavioral biometrics, as offered by Twosense, provides a more adaptive and continuous approach, ensuring that the person behind the keyboard is who they claim to be, all day, every day.
Ultimately, the threat of malicious insiders—whether motivated by personal gain or external influence—requires a multifaceted defense strategy. By embracing innovative solutions like behavioral biometrics, BPOs can protect their business, clients, and reputation from the unseen dangers lurking in the shadows of remote work.
Ready to fortify your BPO security? Schedule a live demo to see Twosense in action and learn how we make securing your contact center simple, scalable, and compliant.