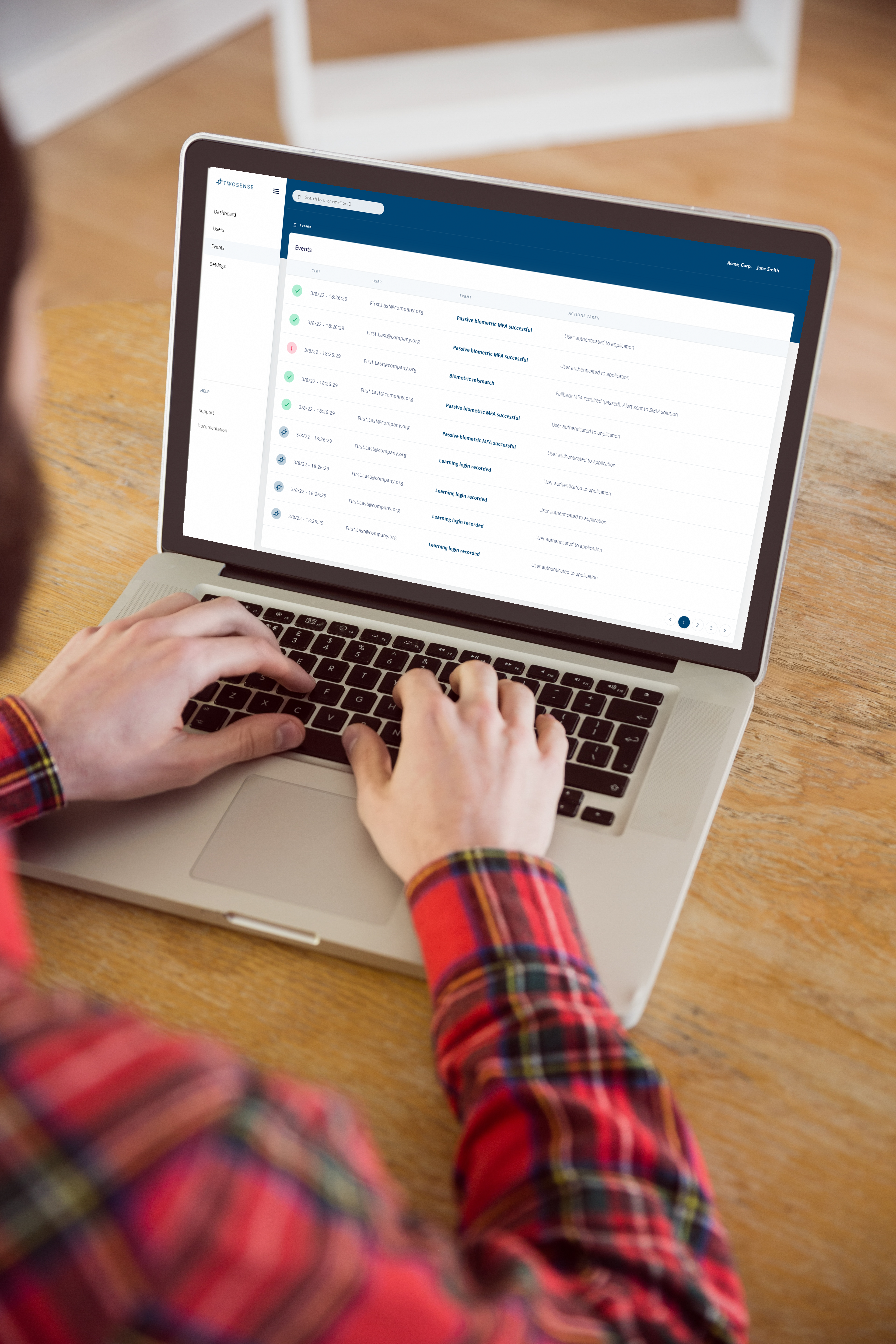
Automated MFA
BLOG LISTINGS
April 2, 2025
The Limitations of Traditional MFA in Contact Centers For a long time, most contact centers have used hard tokens to...
December 23, 2024
Cybersecurity in contact centers isn’t just about locking down systems—it’s about protecting agents and data without...
December 11, 2024
As the cost of data breaches increases annually, contact centers are constantly exploring new solutions to enhance the...
October 30, 2024
With cyber-attacks on call centers on the rise, businesses are forced to explore solutions to enhance the security of...
September 5, 2024
BPOs need help with data security: faced with a mountain of challenges, they must secure their operations without...
December 18, 2023
In the rapidly evolving landscape of cybersecurity, the need for robust authentication measures is paramount. As BPOs &...
Posts by Tag
- 2FA (8)
- Agent Identity (4)
- Agile (1)
- Automated MFA (6)
- Behavioral Authentication (3)
- Behavioral MFA (27)
- Biometrics (19)
- BPO (22)
- Burnout (1)
- CCaaS (1)
- Clean Desk MFA (1)
- Compensating Controls (2)
- Compliance (18)
- Contact Centers (49)
- Continuous Authentication (63)
- Continuous MFA (26)
- Cryptocurrency (1)
- Culture (3)
- Cyber Insurance (1)
- Cybersecurity (27)
- Data Breach (12)
- Data Science (1)
- Deep Work (1)
- Flow State (1)
- Hard Token Alternative (1)
- Hard Tokens (1)
- Identity Access Management (1)
- Infosec (14)
- Machine Learning (5)
- Mental Health (3)
- MFA (5)
- Multi-Factor Authentication (47)
- Passive Biometrics (10)
- Passive MFA (1)
- Password Sharing (1)
- Passwordless (1)
- PCI Compliance (18)
- PCI DSS (14)
- Phishing (5)
- Phishing-Resistant MFA (10)
- Preparedness (1)
- Prompt Bombing (3)
- RFPs (1)
- SOC2 (1)
- Social Engineering (4)
- Software MFA (1)
- Twosense Team (2)
- Unauthorized Users (1)
- Unphishable MFA (11)
- WAHA (1)
- Webinar (1)
- WFH (4)
- Zero Trust (10)
Recent Posts
Sign Up for our Blog
We will never share your email address with third parties.