The pandemic pushed all businesses that could to a work-from-home model, and contact centers were no exception. Initially, many were uncomfortable with the work-at-home-agent (WAHA) model, mostly due to security concerns. Over time, compliance auditors and contact center operators found ways to meet in the middle and make WAHA models successful. PCI 4.0 is bringing new scrutiny and requirements to agent security, which will throw a major wrench in the gears of new and existing contact center businesses, particularly for WAHA business models and especially for outsourced BPO contact centers. We’re going to look at why here.
Requirement 8.4.2 is where this series will begin. As discussed last week, while compliance tends to be dry and complicated to interpret, the PCI SSC has made its position on MFA clear in PCI 4.0: deploy MFA to everyone, everywhere.
8.4.2 MFA is implemented for all access into the CDE.
“If an individual first connects to the entity’s network via remote access, and then later initiates a connection into the CDE from within the network, per this requirement, the individual would authenticate using MFA twice”
This means every individual –agents, vendors, and third parties– will be required to authenticate when accessing a VPN, again to access the CDE, and again for all applications. An additional measure was added to clarify that completing an MFA challenge into any system does not mean you can forego authenticating into the others. This means that even after that first MFA, MFA is required again for each access request to the card data environment (CDE).
8.4.1 Administrative access to the CDE cannot be obtained by the use of a single authentication factor.
If you are reading between the lines here, you know this presents one significant problem– security friction. This friction will only increase as requirements compound upon one another– which we will discuss in the next blog.
Sign Up For Full Access To The Blueprint To PCI DSS v4.0 Multi-Factor Authentication.
Implementing these new standards will significantly increase agents' time interfacing with MFA. Agents will be required to authenticate into their primary system or VPN, again to enter any cardholder data environments, and into every application required to perform their job.
This will be challenging from an implementation perspective but will also impact the bottom line. What used to be a single sign-on event for an agent to start a shift will now be a complex, multi-stage process taking considerable time. Furthermore, as we’ll talk about later in this series, this process will now have to be repeated several times throughout a single day. For every hundred agents, thousands of minutes each month will be spent on MFA challenges instead of calls. The more time agents spend authenticating into systems, the less time they can spend with customers. Also, as every IT practitioner knows, every interaction with authentication can result in a problem, and many more authentications mean many more helpdesk tickets.
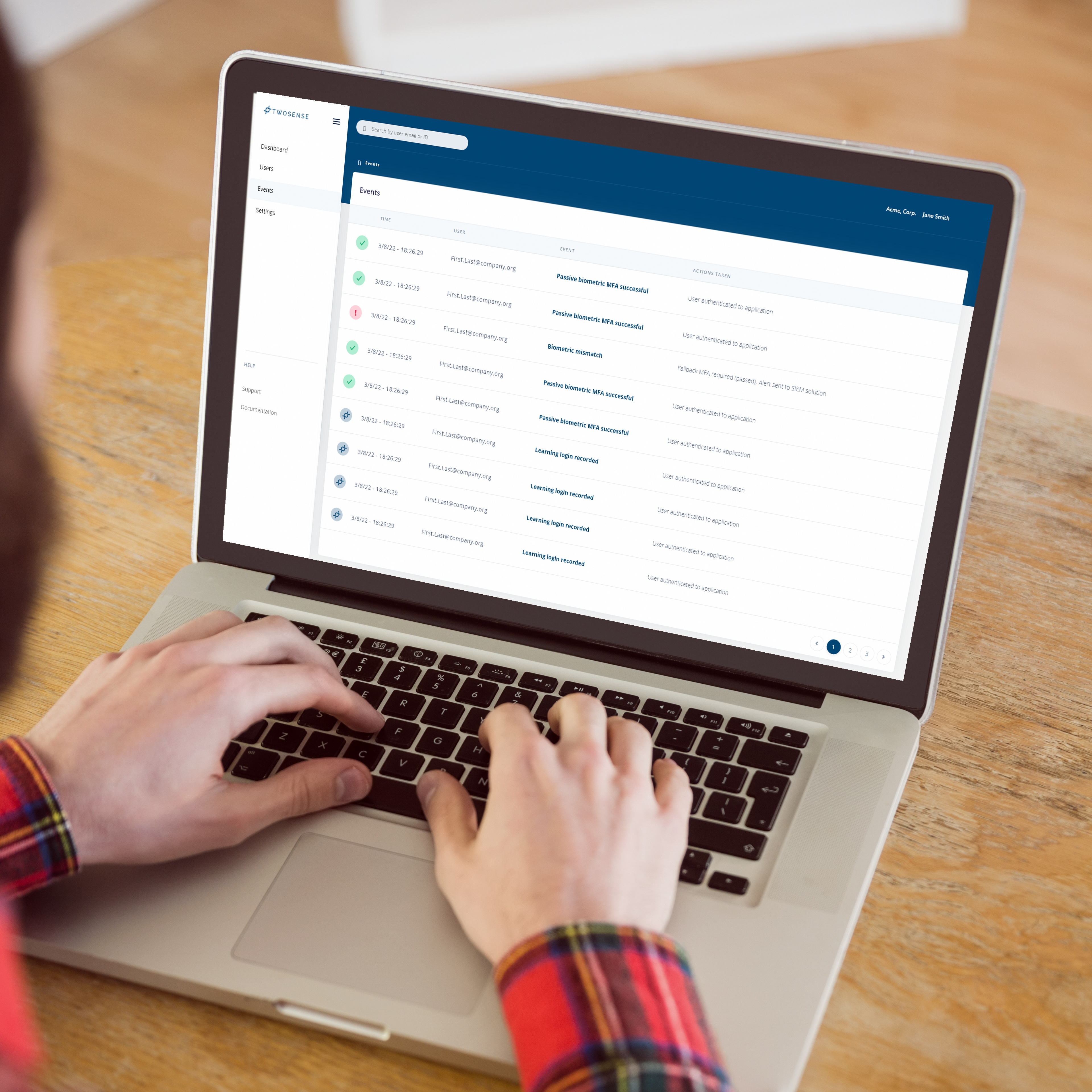
How do BPOs move forward in a way that will meet compliance standards and mitigate security friction? The solution is simple: deploy an identity security MFA solution capable of invisibly authenticating agents in zero time without sacrificing security.
This is where Twosense can help contact centers. With behavioral biometrics Twosense can validate an agent's identity and authenticate them not by what they’re doing but by how they’re doing it, generating a level of trust for every interaction in the background. That trust score is then used to authenticate the user continuously throughout the day or flag suspicious behavior. Continuous MFA authenticates on endpoints, web, and Single Sign-on, getting BPOs PCI 4.0 compliant with MFA everywhere and all the time.
Twosense Continuous MFA is PCI 4.0 compliant and doesn’t require hardware. That means no enrollment is necessary, making deployment to agents simple. Once the Twosense agent is installed on each user’s machine– which is three easy steps– no further action is required.