Biometric technology today has become increasingly versatile in its applications – and whether you realize it or not, biometric technology is something that most of us use daily. From facial recognition on social media to the fingerprint tech that keeps the confidential information on our mobile devices secure. But many are still asking, what is biometric technology and how does it work? First, let's discuss the different types of biometrics. There are active and passive biometrics, and there are physiological and behavioral biometrics.
Active biometrics rely heavily on physiological components: fingerprints, hand geometry, and retina scanning. They also require some sort of user participation, from intentionally putting your finger on the appropriate place on your device to holding the camera in the right position for retina scanning.
Passive biometrics measure something that is intrinsically part of an individual without requiring any action on the part of the user. Behavioral biometrics are one form of passive biometrics that take into consideration the way a user types, the rhythm in which they use a keyboard, their stride and footfall, or the gestures they use when scrolling on their phone. These “passive” or behavioral biometrics are done instinctually.
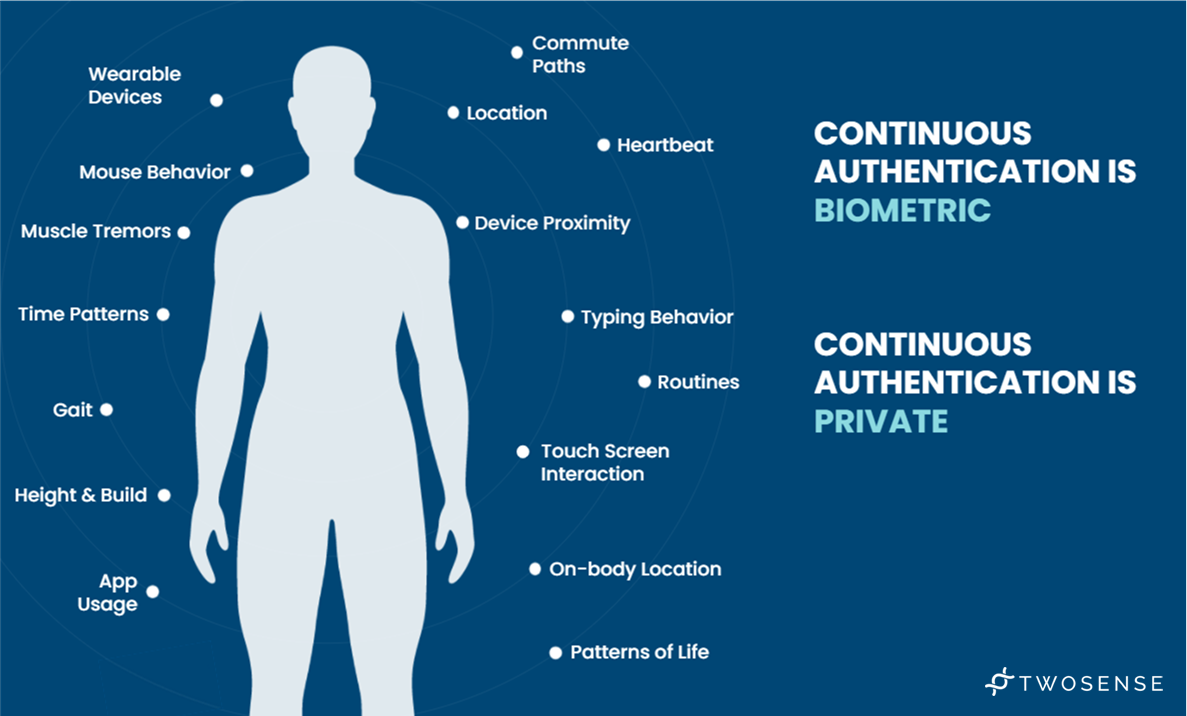
Because of the intrinsic nature of passive biometrics, they have become a fundamental variable in identity security. Twosense, for example, looks at every measurable aspect of human behavior to build a holistic profile of each user, which we refer to as “the model”. Twosense uses motion sensors to observe a user’s gait, quantifying aspects such as their stride length and impact of footfall. With respect to a user's typing behavior, Twosense quantifies aspects such as speed, cadence, variability, and errors specific to each user.
With the implementation of AI and machine learning, passive biometrics have become essential when developing security policies because they cannot be fabricated. While traditional MFA focuses on something that you know (login and password) or something you have on your person (mobile device), it still leaves significant room for security breaches. Passwords and devices can be stolen or lost, tokens can be phished, but replicating another person's behavior identically is impossible.



