With cyber-attacks on call centers on the rise, businesses are forced to explore solutions to enhance the security of their operations. However, security and convenience have a complex relationship, and experience has shown that one without the other just won’t work. Robust security measures often inconvenience users, and too much inconvenience makes users bypass or find workarounds to security measures.
Unfortunately, modern cyber-attacks rely on the complexity of security systems and the inconvenience they create to nudge users into allowing bad actors into the system. Even as concepts like continuous access evaluation appear to be effective at keeping threats at bay, the complexity and the difficulty of using them continue to be a security threat.
In this article, we explore the drawbacks of existing multi-factor authentication solutions and how Twosense may be the solution organizations are looking for.
What Are The Drawbacks Of The Common MFA Solutions?
One of the main problems with MFA is that it is annoying. This creates a security issue. When a user is forced to authenticate multiple times or through multiple modes, they tend to devise workarounds for them. For instance, if a user is forced to enter multiple passwords, they may write it down on paper.
Bad actors exploit this “MFA fatigue” to access otherwise secure systems. One of the common ways in which attackers overcome MFA is through MFA bombing, in which they send many multi-factor authentication requests over extended periods of time. This may cause the user to accidentally accept an authentication request on their phone by clicking the wrong button or thinking there is a bug in the MFA system and receiving the request.
When you consider that almost 98% of all attacks involve social engineering, MFA fatigue presents a severe risk.
Another drawback is that security policies in many industries cannot allow for some of the usual MFA solutions. For instance, many contact centers that process payment information are subject to a clean desk policy. These organizations don’t allow employees to use their phones at workstations, so authentication apps are not an option.
Most MFA solutions authenticate only at one or two points, typically upon logging in and after idle periods. Once the user logs in, these solutions cannot detect if someone else has taken over the system. While many solutions allow administrators to set up multiple authentications in a workday, it increases security friction. We can’t expect users to authenticate every four or five minutes. And it may not be enough to detect bad actors already in the system remotely. In many cases, detecting a breach takes around six months; during that time, the attacker moves laterally through the system.
Why Do Organizations Need Continuous Access Evaluation?
Traditional authentication solutions that check for access just once or twice are not enough to mitigate the latest threats that enterprise systems face. While many vendors offer solutions requiring employees to authenticate every hour, that may be too long for a bad actor to wreak havoc within the systems.
For instance, from a security perspective, it's crucial to immediately revoke their access to sensitive information if an employee was let go suddenly. Industries such as BPOs and contact centers that face high turnover rates need solutions that can quickly remove access without waiting for the next authentication.
As more organizations move to remote work, there is also the risk that employees may outsource their work. They may just log in and hand over their systems for someone else to work. This presents a huge security risk. Unauthorized and unknown people can access customer information and cause a data breach or even draw penalties from regulatory bodies.
How Is Twosense Better Suited For MFA In Enterprise Scenarios?
One of the main advantages of Twosense over traditional MFA is that it is completely automated and works behind the scenes. Users don’t have to enter passwords, use their fingerprints, or enter an OTP or code.
In addition to convenience, this eliminates user errors and makes Twosense phishing-resistant. Attackers will find it impossible to execute social engineering attacks; they would not only have to trick the users into performing extended and lengthy tasks instead of just entering a password or a code but also replicate the user's behavior exactly–which cannot be done.
Employees in remote environments will also find it increasingly more difficult to outsource their work with Twosense. The solution continuously analyzes users' behavior and can quickly detect if someone else is using the system.
Twosense is also perfect for clean desk environments demanded in many industries since the solution is deployed as software, and the users don’t need their phones or other hardware to authenticate.
How Does Twosense Work?
Twosense started by working with the US Department of Defense to build an authentication solution to replace their secret cards. It uses multifactor behavioral biometrics to authenticate users.
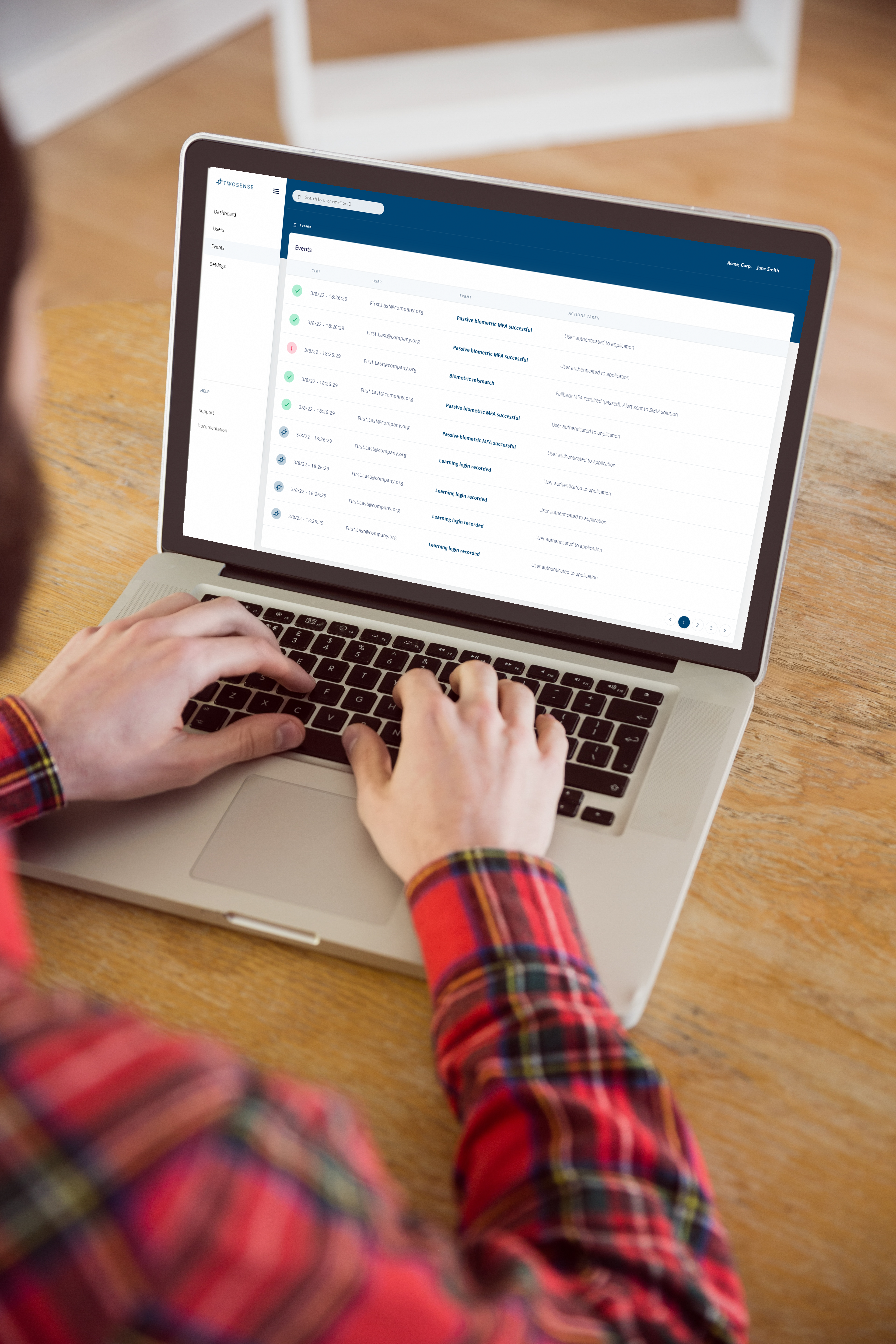
It works by analyzing how a user interacts with their systems. Twosense is deployed as a software that learns how the user uses their keyboard and mouse, interacts with different apps, and other usage patterns. Using this, it builds a “profile” for the user and continuously checks inputs against this to authenticate them. All of this happens behind the scenes with no intervention from the user.
Twosense comes with automated remediation in case of authentication failures. Administrators can configure the system to ask the user for passwords, codes, or other forms of authentication if it detects another entity using the system.
The solution takes around two weeks to build a user profile and understand how they use their systems. After this period, it can detect if someone else is using the system, raise alerts, and take the following steps the administrator has configured.
An exciting aspect of Twosense is that it doesn’t know or record what you’re typing or doing on the system or the apps you’re using. It can know when you’re using different apps and how you interact with them, but it cannot name the apps you used.
How Does Twosense Compare With Hardware Tokens Or Physical Security Keys?
Hardware tokens are another phishing-resistant MFA solution that many organizations use. However, their main drawback is the operational cost associated with them.
In large organizations with many employees, issuing and managing security keys could require significant resources. They will need to keep track of people with security keys and the access these security keys provide and ensure that they’re returned when the employee leaves the organization. High employee turnover in industries like contact centers can lead to substantial operational costs.
These costs can go higher in remote environments.
With Twosense, organizations can deploy behavioral biometric authentication quickly and with little resources. And unlike Yubikeys or other hard tokens, Twosense can prevent remote employees from outsourcing their work.
Ready For A More Convenient And Robust Authentication Solution?
Twosense offers businesses a perfect blend of security and convenience. The solution is easy for administrators and employees and provides robust protection against cyber threats.

.png)
