In recent events, multiple Twitter accounts have been hacked showing a message using bitcoin as an avenue to obtain funds.
The hack has been possibly traced back to a Twitter employee, rather than a user that had access to a “user dashboard”.
After some internal investigation, Twitter has determined that it is the result of a social engineering attack on one of its employees.
As long as humans are in the loop, there will always be room for error and attacks in an age of digital transformation where attack areas are more porous.
People are traditionally the weakest link in security systems like this. No amount of VPN and MFA/2FA will stop an inside job.
This is why orgs shouldn’t wait to start moving to a Zero Trust Architecture, even if they are now working remote.
One of the easiest ways to start is by implementing Continuous Authentication which can be low lift and accomplished even with a remote workforce.
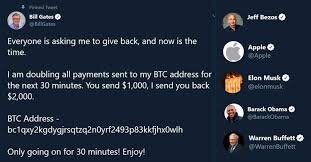
Bill Gates Twitter account hacked to display Bitcoin message
Twitter recently suffered an attack which showed multiple twitter high-profile accounts being compromised including but not limited to Bill Gates, Elon Musk and Barack Obama. This attack was used to post multiple messages duping people into sending more than $100,000 to a Bitcoin wallet (photo on right). Twitter has been conducting an ongoing investigation but so far, they have identified that this was the result of a social engineered attack on one of their employees with access to some powerful tools (photo shown below). This goes to show that no matter how secure an organization thinks they are, the weakest links are always humans.
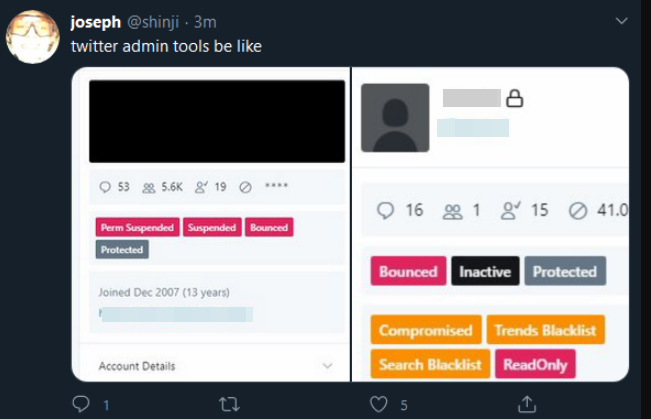
View of internal Twitter admin tools that allowed hackers to compromise accounts
Over 90% of data breaches are not infrastructure related, but rather the result of human error. No amount of VPNs or MFA/2FA will stop an attack when an employee, knowingly or not, has given their access to an outsider. Organizations will now have to ask themselves, not what can they do to improve their infrastructure, rather what can we do to reduce the risk of human error? Especially in a new age of digital transformation where more and more organizations are resorting to remote working, the identity perimeter is no longer solid and physical security is limited.
While there aren’t any concrete answers, it shows why the shift to a Zero Trust Architecture for these organizations is now more important than ever. While seemingly difficult to uphold while working remotely, it’s necessary for orgs to start looking at ways of getting there. Zero Trust assumes that a user has to prove themselves every step of the way and is a deterrent to such threats such as insider threat.
One of the newer areas of Zero Trust is Continuous Authentication, an aggressive approach to authentication. By continuously authenticating your users, you can get more insight into what systems they are trying to access and if it is who they truly say it is. This means that even if someone else manages to get access to an account, whether that be through social engineering or other means, an organization will have insight into whether that access is suspicious and warranted and be able to proactively take action rather than having to deal with the aftermath of a serious breach.
This initiative has long been spearheaded by startups like TWOSENSE.AI using behavioral biometrics, but is now being picked up by Microsoft, Okta, Gartner and others. With Continuous Authentication on its way into the mainstream Enterprise identity stack, hacks like the one at Twitter will be harder to replicate.

.jpeg)
.jpeg)