- The latest attacks are said to be the work of APT29 or Cozy bear, the same hacking group that’s believed to have orchestrated a breach of cybersecurity firm FireEye a few days ago
- Spies are believed to have gained access by tampering with updates released by Texas-based IT company SolarWinds. This attack, commonly referred to as a “supply chain attack”, works by hiding malicious code in legitimate software updates provided to targets by third parties
- FireEye said the supply chain attack takes advantage of trojanized SolarWinds Orion business software updates in order to distribute backdoor called SUNBURST
- The compromise of SolarWinds’ Orion Network Management Products has caused CISA to release an emergency directive, urging federal civilian agencies to review their networks for suspicious activity and disconnect or power down SolarWinds Orion products immediately
- Hackers also broke into the NTIA’s office software, Microsoft’s Office 365, and staff emails were monitored by the hackers for months, maybe even as early as Spring 2020
Just days after the recent FireEye breach, reports have surfaced that the same attackers have managed to breach the US Treasury and the National Telecommunications and Information Administration (NTIA) and have been monitoring emails for months. The attacks are suspected to be the work of APT29 or Cozy bear, Russian state hackers.
The attackers are believed to have gained access the same way they managed to recently infiltrate FireEye, through tampering with updates released by Texas based IT company SolarWinds. This attack, which is commonly referred to as a “supply chain attack” - works by hiding malicious code in the SolarWinds software updates provided to the targets by third parties. FireEye has said that the supply chain attack takes advantage of trojanized SolarWinds Orion business software updates in order to distribute a backdoor called SUNBURST. After a dormant period of up to two weeks, this backdoor retrieves and executes commands, called “Jobs”, that have the ability to transfer and execute files, profile the system, reboot the machine, and disable services.
The compromise of SolarWinds’ Orion Network Management Products has caused CISA to release an emergency directive, urging federal civilian agencies to review their networks for suspicious activity and disconnect and power down SolarWinds Orion products immediately. SolarWinds is said to be used by more than 300,000 customers worldwide, so even for non-federal organizations, they should follow CISA’s instructions.
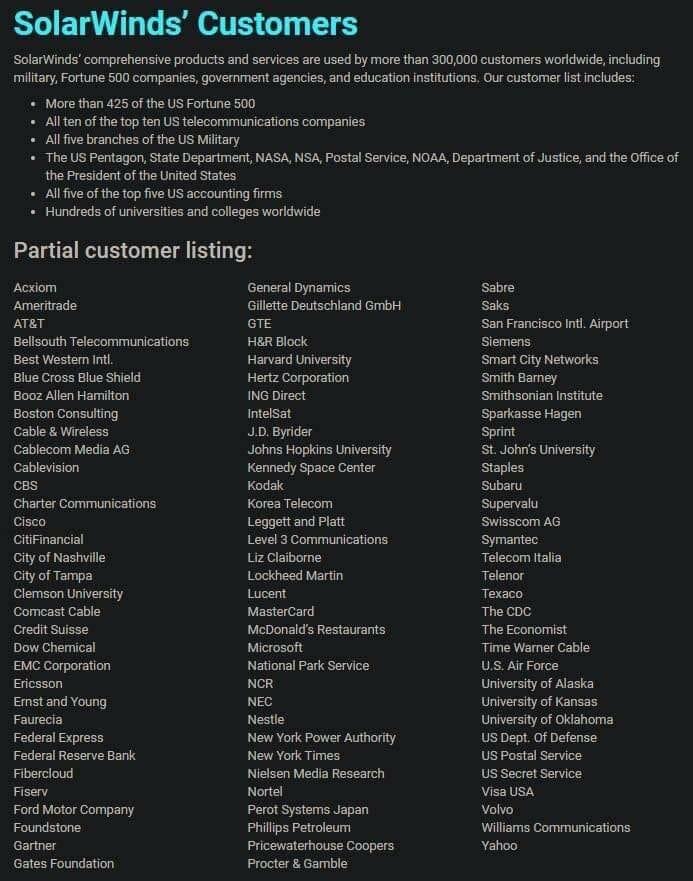
List of potentially affected SolarWinds customers
The attackers also broke into the NTIA’s office software, Microsoft’s Office 365, and staff emails were said to be monitored by the attackers for months. There is some indication that the email compromise of NTIA dates back to this summer, even as early as Spring 2020. It’s said that the attackers managed to bypass Microsoft’s platform authentication controls. Microsoft has recommended actions for organizations to protect themselves from being compromised by these actors, most notably stronger authentication. Microsoft has previously reported that organizations are reluctant to enable MFA, but with these recent attacks, strong MFA is no longer an option but a necessity.
While many organizations have started to enable stronger MFA, there is often a reluctance due to the friction and security fatigue that is associated with an increased amount of MFA prompts. This is why it’s important that organizations start looking into continuous authentication as it’s not only an important component of Zero Trust architecture, but it also alleviates the friction associated with MFA and allows organizations to detect bad actors within their systems. If your organization is thinking about continuous authentication, reach out to TWOSENSE to see how you can get started.



