Go Passwordless and Reduce Failed Clinical Logins by 89%
A Top 5 U.S. hospital secured 17,000 users across shared workstations and nearly 1 million passwordless authentications, all without phones, tokens, or cameras.

Identity That Interferes with Patient Care
Clinicians work in some of the most complex IT environments in healthcare. Shared workstations, session timeouts, and traditional authentication methods create constant friction. Instead of supporting care delivery, identity systems often slow it down and add to clinician burnout.
- 2FA pop-ups and long passwords delay logins
- Mobile phones restricted in many clinical areas
- Facial/fingerprint recognition fails with PPE
- Shared workstations force repeated logins
- Session timeouts interrupt patient care
Automating Authentication with Twosense
Twosense delivers a software-only Continuous Authentication and Continuous Access Evaluation (CAE) platform built for healthcare. It runs invisibly in the background, continuously verifying identity based on behavior. No hardware, no mobile phones, and no cameras. With Twosense, you get secure, frictionless access that works with clinical workflows.
- Continuously Authenticate users with biometric signals such as keystroke timing and mouse movement
- Automated logins with no passwords or mobile push
- Extend session timeouts safely without added risk
- Clinicians spend more time with patients, not passwords
.png?width=1080&height=1080&name=Untitled-7%20(2).png)
Real Impact on Care Delivery
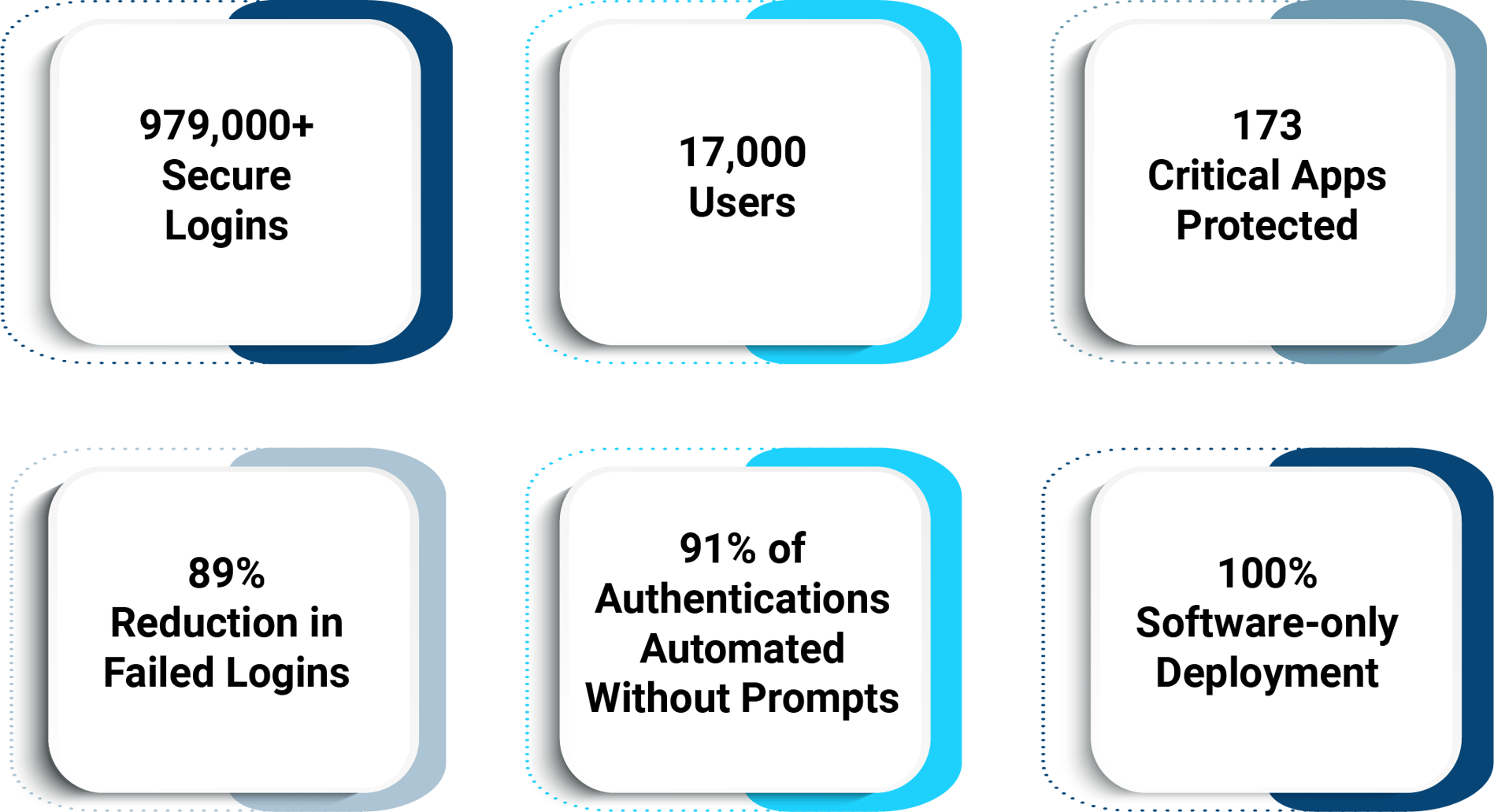
Continuous Authentication Results in a Leading U.S. Healthcare System
A leading U.S. health system secured 979,000+ logins across 173 critical applications for 17,000 users. After just six and a half months, Twosense has reduced failed logins by 89%, automated 91% of authentications, and deployed 100% via software, improving clinician access, compliance, and security in shared workstation environments without requiring hardware or user prompts.
By automating authentication and enabling seamless transitions between workstations, Twosense gave clinicians something they don’t have enough of: time.
.png?width=1080&height=1080&name=Untitled-4%20(1).png)
How it Works
The Twosense Continuous Authentication and Continuous Access Evaluation (CAE) platform operates invisibly in the background, continuously analyzing unique behavioral biometrics, such as keystroke patterns and mouse movements. This creates a real-time "trust score" that automates authentication and verifies user presence throughout their session.
Keep Clinicians Focused on Patients, Not Passwords
Let’s talk about your hospital’s identity challenges and how we can solve them. Get a demo and see how Twosense secures clinical access without slowing it down.
.png)

